Internet threat actors are constantly diversifying their portfolio of attack mechanisms and targets. When it comes to the extortion vector, things no longer boil down to attacking individual computers or enterprise IT networks. In a recent defiant move, a group of hackers have been targeting HPE iLO 4 interfaces. This technology stands for HPE Integrated Lights-Out, a proprietary framework by Hewlett-Packard that allows administrators to access and manage some HP servers remotely. The admin can use their regular web browser to log in and do their settings tweaking or maintenance job, for instance, reboot the server and view details on its current status.
Security analysts have stumbled upon incidents where malefactors replaced HPE iLO 4 login screen with a ransom note named “Security Notice: Basic principles of Data Anonymization”. It says the server’s hard disk is encrypted using RSA-2048 asymmetric cipher, and to decrypt the data the victim needs to obtain the private key. In order to get this secret code, the plagued user is instructed to contact the attacker at 15fd9ngtetwjtdc@yopmail.com and follow the steps provided in a reply. Ultimately, the recover process is a matter of paying 2 BTC (about $19,000) to the crooks’ Bitcoin address.
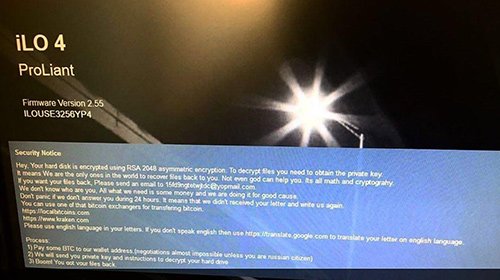
For this complex compromise to take place, the perpetrators need to gain unauthorized access the server interface. To this end, they scan the Internet for online-accessible iLO tools and then leverage brute-force or dictionary attack to get in. Outdated firmware makes the breach easier. Once the stealth login attempt succeeds, the hackers user the iLO 4 Login Security Banner feature to set a custom login screen containing the ransom note. Then, they remotely invoke a command that performs disk encryption via the above-mentioned public key cryptosystem.
Interestingly, the decryption how-to message emphasizes that the negotiations on the size of the ransom are hardly possible unless the victim is a Russian citizen. This nuance gives some clues regarding the background of the attackers. All in all, this compromise is a serious predicament that may end up ruining data stored on a vulnerable HP server. Administrators should therefore add some extra security layers to their login process. In particular, the firmware should be up to date at all times, the server’s IP address shouldn’t be left accessible via the Internet, and the login routine should involve a reliable VPN solution.
